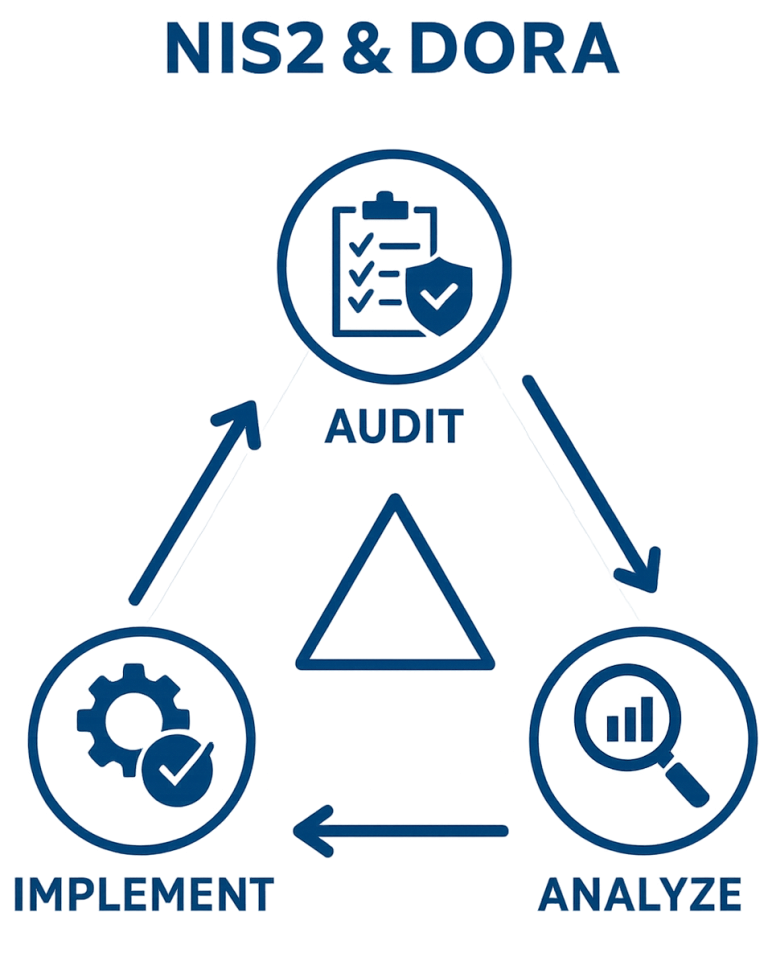
NIS2 and DORA compliance framework: Audit, Analyze, Implement
In today’s digital landscape, the NIS2 and DORA compliance framework no longer represents an abstract set of rules—it forms the backbone of modern digital resilience. Moreover, cyber threats and operational risks grow more complex every day, so organizations that take compliance and risk management seriously must move beyond checklists. Therefore, they need to think in…